Magento is an open-source platform that consists of all leading cutting edge functionalities in one pack. But using an open-source platform has always drawback that is code is openly available to all which is like open invitations to hackers and attackers. And security is one of the important factors for any Ecommerce stores. Having wide Magento Community, Magento Developers are working hard to improve and enhance CMS with their regular updates. For new Magento version it by default includes all security enhancement but what about old Magento stores? To protect each store Magento is always releasing small security patches or you can say SUPEE that contains bug fixes and security enhancement to protect your store from vulnerabilities.
But why it is important to apply these security patches to your Magento Store?
In the year 2015, Check Point researchers discovered a critical remote code execution (RCE) Hazard in Ecommerce platform Magento which can bulge to outright compromise of any Magento store, which may include personal data, credit card info and other data which can affect nearly 200 thousand online shops.
So, we always recommende store owner to upgrade their store but if you dont want to upgrade your store so frequently one should have to install security patches to keep their store secure and up to date.
Magento has already released one patch last year, but 80% of Magento stores haven’t applied and so those were vulnerable, so Magento have to send notification to install patches and make your Magento store secure. This Remote code vulnerability was originally founded by Check Point and reported about the issue to Magento.
We have covered the installation fo following patches but you can install other using the same method:
- SUPEE 1533
- SUPEE 5344
- SUPEE 5994
- SUPEE 6285
- SUPEE 6482
- SUPEE 6788
- SUPEE 7405
- SUPEE 7616
- SUPEE 8788
- SUPEE 9652
- SUPEE 9767 – NEW!
- FAQs
Refer this awesome spreadsheet to know which patches your Magento needs. This sheet is prepared and maintained by JH.
How your store can be hacked?
Hacker can run the malicious code and try to create one fake admin user with all rights in the Magento database leveraging SQL injections. If you think, your website has been hacked, then please try to find usernames in your database: admin_user and ypwq, as these are the names hackers are using so far.
Why You should fix this as soon as possible?
Check Point researchers recently discovered a critical RCE (remote code execution) vulnerability in the Magento web e-commerce platform that can lead to the complete compromise of any Magento-based store, including credit card information as well as other financial and personal data, affecting nearly two hundred thousand online shops.
Source: http://blog.checkpoint.com/2015/04/20/analyzing-magento-vulnerability/
SUPEE 1533 & SUPEE 5344
Magento has released these 2 patches, SUPEE-1533 and SUPEE-5344.
The important thing is now how to install the patches for the Magento website, here is the simplest guide to apply patches on your magento.
There are 3 ways to install patches, either using SSH and the other one is using FTP or cpanel. Some hosting provider don’t provide the SSH access for your plan, but don’t worry you have other option to follow.
Compilation:
Make sure compilation has been disabled in your store before installing patches. If you haven’t disabled the compiler and installed the patch, test everything and run the compiler to again. It needs to run the compiler to take effect of the code of the patch.
I have explained installation of patches with both the ways here:
Follow this instruction to install patch on your store,
Method 1:
-
-
- Upload patch files in the root of magento.
- Make one file with the name of patch.php, write following code in it,
-
<?php
print("<PRE>");
passthru("/bin/bash PATCH_SUPEE-5344.sh");
print("</PRE>");
echo "Done";
?>
Replace the file name in it, upload it in the root and run the file from the browser.
Name should be PATCH_SUPEE-5344.sh or PATCH_SUPEE-1533.sh
You should receive following screen once you run patch.php from the browser,
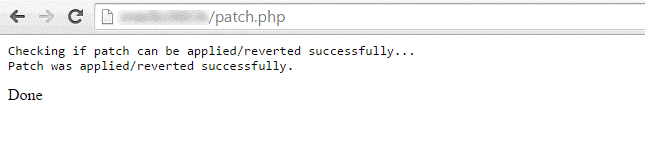
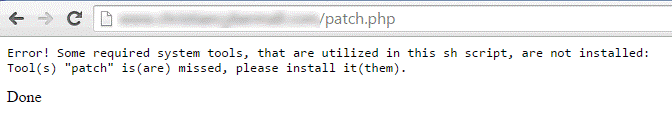
If you are getting error like this,
“Error! Some required system tools, that are utilized in this sh script, are not installed; Tool (s) “patch” is (are) missed, please install it(them).
That means system tools aren’t installed in your server to run the sh script, you can contact your hosting provider or follow another method.
We have updated the patch files for the older Magento versions:
It is very much recommended to use this patches at your own risk, please take backup of your website. It is highly recommaded to upgrade your Magento version to latest one, you can contact us for the Magento Upgrade Service.
You can install patch with SSH as well. You will need SSH, if you don’t know how to set up SSH, contact your hosting provider.
-
-
- Upload the patch files in the root,
- In ssh console, run the command as following.
-
For .sh file extension
Sh PATCH_SUPEE-5344.sh
Sh PATCH_SUPEE-1533.sh
For .patch file extension:
patch —p0 < patch_file_name.patch
Method 3:
We have uploaded the zip files with already patched files, you will just need to extract and upload It in the root of your Magento.
Patch SUPEE-1533 (Magento 1.7.x.x-1.9.1.0) applied to the following files:
-
-
- app/code/core/Mage/Adminhtml/Block/Dashboard/Graph.php
- app/code/core/Mage/Adminhtml/controllers/DashboardController.php
-
Patch SUPEE-5344 applied to the following files:
-
-
- app/code/core/Mage/Admin/Model/Observer.php
- app/code/core/Mage/Core/Controller/Request/Http.php
- app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php
- app/code/core/Mage/XmlConnect/Model/Observer.php
- lib/Varien/Db/Adapter/Pdo/Mysql.php
-
You can also download these Pre Patched files from GitHub.
NOTE : Please Don’t forget to check the user account for the admin, if you found any malicious user accounts, delete those immediately.
Check your Latest Security Patch status at: http://magento.com/security-patch
SUPEE 5994
Magento released this patch on 14th May, 2015. This Patch stuffs several vulnerabilities, one of which is the possibility the download the customer data allow.
Here is the way to install the patches:
Method 1:
-
-
- Download the latest patch SUPEE 5944 from the Official Magento website: https://www.magentocommerce.com/products/downloads/magento/
- Upload the downloaded patch file in the root of your Magento, Make sure it has full permissions to execute.
- Make sure compiler has been disabled, (if enabled and patches installed then may show errors)
- Install the patches using SSH (if you have access, if you don’t have ask your hosting provider to give)
Run the command: sh file_name.sh
Example: sh PATCH_SUPEE-1868_CE_1.7.0.2_v1.sh - Clear the Cache
Refresh your cache from the Magento admin, Don’t forget to refresh your OPcode or APC cache as well! (If not done this can create issue for you)
-
Currently there isn’t any way to verify that SUPEE 5994 installed or not but we are working on our Magento Applied Patches extension so that you can check.
Method 2:
As per our promise, here are zip files for the SUPEE 5994 Patch. You can also download these Pre Patched files from GitHub.
You can also check yourself which patches have been installed in your Magento Store with this extension(only if you have installed using SSH or using Patch.php file upload method): https://www.magecomp.com/magento-applied-security-patches.html
SUPEE 6285
Magento Security Patch SUPEE 6285 addresses the following security issues:
-
-
- It prevents attackers from posing as an administrator to gain access to the last orders feed, which contains personally identifiable information that can then be used to obtain more sensitive information in follow-on attacks. Check to see if you have been compromised by reviewing your server logs for someone trying to reach the /rss/NEW location.
- It closes a number of security gaps including cross-site scripting (XSS), cross-site request forgery (CSRF), and error path disclosure vulnerabilities.
-
Method 1
You can follow the same process as stated above for SUPEE 1533, 5344 nad 5994
Method 2
You can follow the same process as stated above for SUPEE 1533 and 5344
Method 3
Download the zip file for the patch installation. You can also download these Pre Patched files from GitHub.
SUPEE 6482
This patch addresses two issues related to APIs and two cross-site scripting risks. Packages of this patch are available now to download.
Method 1
You can follow the same process as stated above for SUPEE 1533, 5344 and 5994
Method 2
You can follow the same process as stated above for SUPEE 1533 and 5344
Method 3
Download the zip file for the patch installation. You can also download these Pre Patched files from GitHub.
SUPEE 6788
We have moved SUPEE 6788 section to: How to install SUPEE 6788 with or without SSH
SUPEE 7405 & SUPEE 7405 v1.1
We have moved SUPEE 7405 section to: How to install SUPEE 7405 with or without SSH
SUPEE 7616
We have moved SUPEE 7616 section to: How to install SUPEE 7616 with or without SSH
SUPEE 8788
We have moved SUPEE 8788 section to: How to install SUPEE 8788 with or without SSH
SUPEE 9652
We have moved SUPEE 9652 section to: How to install SUPEE 9652 with or without SSH
SUPEE 9767
We have moved SUPEE 9767 section to: How to install SUPEE 9767 with or without SSH
[expand title=”1) I’ve installed the patches as instructed, but the warning still keeps showing when I log into Magento admin panel.“]
Warning is just the notification, you can “mark as read” all those messages if you have successfully installed the patches. If you haven’t either follow the blog post, or do contact us, we will help you with the patch installation for FREE [/expand]
[expand title=”2) I’m on a shared server and my hosting provider does not allow access via SSH or telnet. Is there another way to install security patches?“]
We have displayed 2 more methods for the security patch installation, try any one of them. If you know about the FTP, then the File upload method is the best. Make sure you take backup of the files you are overwriting. [/expand]
[expand title=”3) Fatal error: Class ‘Mage_Install_Controller_Router_Install’ not found
Warning: include(Mage/Install/Controller/Router/Install.php) function.include:failed to open stream: No such file or directory“]
-
-
- Have you switched off and cleared compilation?
via the console/ssh you can use
$ php -f shell/compiler.php — disable
$ php -f shell/compiler.php — clear
$ php -f shell/compiler.php — compile
$ php -f shell/compiler.php — enable - Check to see if the file app/code/core/Mage/Install/Controller/Router/Install.php exists.When you ran the patch, the directory Router didn’t exist in app/code/core/Mage/Install/Controller and so the Install.php file did not get created despite being told otherwise in the applied.patches.list file. This means you’re missing a class and you get the message:
- Have you switched off and cleared compilation?
-
[/expand]
[expand title=”4) blank page after installling security patch PATCH_SUPEE-5994“]
a. Make sure there is a install.php file at this path app/code/core/Mage/Install/Controller/Router/Install.php
with a capital “I”? If not, rename it, so it will start with a capital “I”.
b. Follow the steps shown in question 3
c. Disable the compiler, here is a way to disable without accessing backend.
Find the file config.php in the directory includes. It will look like this:
<?php ...
define('COMPILER_INCLUDE_PATH', dirname(__FILE__).DIRECTORY_SEPARATOR.'src');
define('COMPILER_COLLECT_PATH', dirname(__FILE__).DIRECTORY_SEPARATOR.'stat');
..
comment out both lines like this:
# define('COMPILER_INCLUDE_PATH', dirname(__FILE__).DIRECTORY_SEPARATOR.'src');
# define('COMPILER_COLLECT_PATH', dirname(__FILE__).DIRECTORY_SEPARATOR.'stat');
try again. You will probably be able to login now. Go to your tools, rerun compilation process and when you get a success, go back to your includes/config.php file and uncomment the lines again.
[/expand]
[expand title=”5) Getting: Error! Some required system tools, that are utilized in this sh script, are not installed: Tool(s) patch is(are) missed, please install it(them).“]
-
-
- For windows server: If you can’t run .sh files (in Windows), then you could extract the second section of the patch (the unified patch) and apply it manually with a patching tool (or for example through PHPStorm).
- For linux server:
The solution is to install the patch package:
yum install patch
Then run sh the patch file:
sh PATCH_SUPEE-1533_EE_1.13.x_v1-2015-02-10-08-18-32.sh
-
[/expand]
[expand title=”6) How can I make sure that SUPEE 1533 and SUPEE 5344 have been installed perfectly?“]
You can check your website for vulnerability here,
https://magento.com/security-patch
You can use our Free Magento Applied Patches extension for the verification.
This extension will only show the result if you have installed the patches using SSH or php file method.
[/expand]
[expand title=”7) How can I make sure that SUPEE 5994 has been installed perfectly?“]
There is no perfect tool to analyze for SUPEE 5994 verification but you can check the files which patch have modified,
-
-
- app/code/core/Mage/Authorizenet/controllers/Directpost/PaymentController.php
- app/code/core/Mage/Core/Controller/Varien/Router/Admin.php
- app/code/core/Mage/Core/Controller/Varien/Router/Standard.php
- app/code/core/Mage/Customer/Model/Customer.php
- app/code/core/Mage/Dataflow/Model/Convert/Parser/Csv.php
- app/code/core/Mage/ImportExport/Model/Export/Adapter/Csv.php
- app/code/core/Mage/Install/Controller/Router/Install.php
- app/code/core/Mage/Install/etc/config.xml
- app/code/core/Mage/Sales/controllers/Recurring/ProfileController.php
- downloader/Maged/Model/Connect.php
- downloader/Maged/View.php
- downloader/template/connect/packages_prepare.phtml
- downloader/template/messages.phtml
- get.php
- lib/PEAR/PEAR/PEAR.php
- lib/PEAR/PEAR/PEAR5.php
- lib/Varien/Io/File.php
-
[/expand]
[expand title=”8. I am getting this error while applying patch? What could be the issue?
Hunk #1 FAILED at …1 out of 1 hunks FAILED — saving rejects to file.“]
The error you are facing is due to the spacing issue in code, we have mentioned this before as well, in patch files, it has been set that at this line, particular code needs to be changed, if patch doesn’t find the code at specified line it throws this error.
Every code line had a CRLF line (empty line) under it. This could be the reason for this error. You will need to find the file and remove this lines between code from files. In short file needs to match exactly what Magento has in its repository for the patch to apply.
Solution: Download the same exact core files for that particular Magento version fresh from the Magento site and replace them with the old core files, the patch will work perfectly.
Or try this one
Run dos2unix command to convert all line endings to UNIX from DOS
Command
~/bash$ dos2unix
For Example : ~/bash$ dos2unix app/code/community/OnTap/Merchandiser/controllers/AdminhtmlController.php
[/expand]
If you have any difficulties with applying the patches please let us know in comments.












HI,
I am extremely sorry as I have not mentioned the website as it not my own, and my friend owns it. The magento version is 1.7.x.x
Further, I tried to use the patch with Method 3, however after the patch, it still shows that the website is VULNERABLE.
I have tried to copy the files as mentioned to the folders using FTP / in
public_html/app/code/core/Mage/Adminhtml/Block/Dashboard/Graph.php
public_html/app/code/core/Mage/Adminhtml/controllers/DashboardController.php
…. but after testing it still shows VULNERABLE. I even waited 1 hour but the result is same. Please Help !! Also I want to know that there are two folders similar to each other which is public_html and www. Do I need to copy the files in both !!!
Thanks
Hello Eshaan,
Have you installed both the patches we have given to download?
Once installed, clear your cache and then test it.
Thank you ! I’m from Brazil and your article helped me a lot !
You are most welcome :):)
Hello,
thanks a lot. Does Method 3 for patch SUPEE-5344 also work for 1.7.0.2? Because it says 1.8-1.9 only above.
Hello,
No we haven’t made package for the 1.7.0.2. We will update the package for it soon. However it is also recommended to upgrade your Magento version to the latest one. You can contact us for help.
Found your post very useful. Thanks!
Instructions and files for version 1.7.0.2 would be highly appreciated!
I’ve tried :
—————————————
Patch SUPEE-5344 (Magento 1.8.x.x-1.9.1.0) applied to the following files:
app/code/core/Mage/Admin/Model/Observer.php
app/code/core/Mage/Core/Controller/Request/Http.php
app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php
app/code/core/Mage/XmlConnect/Model/Observer.php
lib/Varien/Db/Adapter/Pdo/Mysql.php
Download the zip from here : SUPEE-5344.zip
—————————————
but not throwing any errors or anything I noticed, but from previous comments, i guess it won’t really fix it for version 1.7.0.2 .
Thanks in advance!
Hello @Mike Kang
Did you test your website here? https://shoplift.byte.nl/
What it is showing?
Hi.
i am following your method-3.
i have magento 1.9.0.1 version. so, i should install both the patches SUPEE-1533 & SUPEE-5344 (your zip files above) ?
or only Patch SUPEE-5344 is enough ?
i m new to magento.
thanks
Shafiullah
Hello Shafiullah,
Yes, even if you are using latest Magento version, you will need to install both the patches to secure your website from vulnerability.
thanks a lot.
Updated Patch files for Magento version 1.6 and 1.7
Hello, thank you for this post. I am having some trouble and I hope you can help.
patch 1533 was successful but patch 5344 gives me this error:
Checking if patch can be applied/reverted successfully…
ERROR: Patch can’t be applied/reverted successfully.
patching file app/code/core/Mage/Admin/Model/Observer.php
patching file app/code/core/Mage/Core/Controller/Request/Http.php
patching file app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php
patching file app/code/core/Mage/XmlConnect/Model/Observer.php
patching file lib/Varien/Db/Adapter/Pdo/Mysql.php
Hunk #1 FAILED at 2834.
1 out of 1 hunk FAILED — saving rejects to file lib/Varien/Db/Adapter/Pdo/Mysql.php.rej
Done
Hello @Nick,
Yes sometimes 5344 patch gives such error,
Please try with method 3.
Use https://shoplift.byte.nl/ to see if the patches have been applied succesfully.
Very usefull this blogpost(s) !
In the 1.7.x.x zip file for SUPEE-5344 patch, the file
app/code/core/Mage/XmlConnect/Model/Observer.php
seems missing ?
Thanks !
Hello @Steph,
There is no need of there in magento 1.7
First and foremost, THANK YOU for the support and information!!
What I don’t understand is why not apply the PATCH_SUPEE-4829 patch… well for that matter, why didn’t Magento just post this as an automatic update? I’m new to Magento, coming from the Joomla world and these patches would have been automatically populated as an update.
Also I noticed that XMLConnectV24 was updated, does that need to be manually patch.
Thanks!!
Charlie
Hello @Charlie,
PATCH_SUPEE-4829 is for the issue in which product images become larger when a shopper selects a swatch on a search result page, if you are aware with the swatch feature of Magento 1.9 and if you are using it, you can apply this patch.
Patches given in this blog are security patches which must needs to be installed, as those patches addresses potential remote code execution exploit. Those are necessary to prevent your Magento store and keep your magento secure from hackers.
Magento is supposed to release next update 1.9.2.0 including this patches. We will keep you updated with the news.
When you say upload into your root directory – do you mean upload the whole file i.e. supee_1533.zip or do I extract the individual graph.php and dashboard controller.php files and replace them. Novice alert!
Hello @Colin,
Please extract the folder whole folder and upload it in the root. I would suggest you to keep backup of your website. If you can upload the files one by one at specific path, you can take backup of each files and upload.
Let us know if you face any problem, we will be happy to help you.
How do I know it has been installed properly? After I ran the ssh commands I got the message: “Patch was applied/reverted successfully.” But is there somewhere in the dashboard or code that will show it has been applied? Thanks.
Hello @bright,
Make sure you have applied both the patches, once applied, you can check your website here https://shoplift.byte.nl
hi
thank you for your post , it help me a lot
on the comment part you said you are going to update method 3 for magento ce 1.7.0.2 , so any where i can find this post after you update , it will be add into this post ? or some where else ? than you
Hello @sam,
We have already updated the blog with the patch files for 1.7, Please check
I tried using method 3, but when I downloaded the zip for 5344 there was no app/code/core/Mage/XmlConnect/Model/Observer.php? I loaded both the 1533 and all but the one listed. My hosting company already tried to add the patches and was unsuccessful. Now my site gives me the following error and I am unable to access anything in the dashboard. Error: Fatal error: Class ‘Magpleasure_Filesystem_Helper_Data’ not found in /home/designso/public_html/app/Mage.php on line 546
Do you have a suggestion for a novice.
Hello @Tina
Please contact us at support@magecomp.com, our technical support team will help you to resolve the issue of the website and with installation of patches as well.
Hello.
I use method 3 to patch my magento site. After i patch it I am still getting this message “WARNING The Magento shop at bikec.si is VULNERABLE to the Shoplift bug. You should fix it ASAP.” from https://shoplift.byte.nl/.
I try to patch it over SSH and i get message “patch applied…” but on https://shoplift.byte.nl/ i am still getting message that magento is vulnerable. What could be the problem?
THANKS A LOT.
Kind Regards,
David
Hello @David,
Please make sure you have installed the both the patches perfectly according to your Magento version. If you are still facing issue, do contact us, we will be happy to help you out.
Hello,
I have applied the both patchs SUPEE-1533 and SUPEE-5344 on a Magento ver. 1.8.1.0 with different methods but the site is still vulnerable in the page test.
Furthermore when we applied the patch SUPEE-1533.zip the graph in the dashboard doesn’t work.
We have installed the both patchs on another magento with version 1.7 and it works.
Do you have a solution?
Thanks
Hello @Christophe
Did you make sure you have installed the patches for the Magento version you have? One of the patch must not be installed successfully. Please try one more time or contact us at support@magecomp.com for further help.
After installing patches, we can’t log in to the admin panel. It refuses our names and logins. What do you think happened.
Hello @Sheryl,
Did you make sure you have installed patches of the Magento version you are using? Please remove cache and session from the cpanel once. Are you getting any error on the homepage?
I tried using method 1 and set up a patch.php file, uploaded patches 1533 and 5345. Entered the code above and amended to path 1533.
I ran the patch in the browser and it comes back with,
Warning: passthru() has been disabled for security reasons in/home/xxxx/public_html/patch.php on line 3
What does that mean, I haven’t tried the same for patch 5345 yet, please help, I need it.
Hello @Asha
Remove the passthru string from the disable_functions at php.ini* file if you have access if you don’t you can ask your hosting provider for the help
Ok I have now located php.ini file to remove the passthru string, however, does that mean that I just delete the word passthru from the following,
disable_functions = popen,exec,system,passthru,proc_open,shell_exec,show_source,phpinfoextension=mcrypt.so
Or do I need to do something else, sorry very new to this.
Hello @Asha,
You can comment that line for now, please keep backup of the file or do remember the change you do. Try then installing the patch and let us know how it goes.
Hi there, I have already commented that line and removed the word passthru, I then ran the file in browser and same error appeared, passthru has been disabled…….. ???
Hello @Asha
Did you restart the apache server then?
Thankyou vey much, now it’s ok with Method 3:
You are most welcome 🙂 You can contact us for any help with Magento Extensions and Custom Magento development. We will be happy to help you 🙂
Have applied the patches as in option 3. Firstly did this on my test site and worked straight away.
Then went to main site did the same and patches show as updating and dates/ times show as updated . However when I check on the https://shoplift.byte.nl my main site shows as still VULNERABLE.
Have redone a few times and cleared Cache in admin and also have followed the tip of re-compiling the Magento PHP compilation (System -> Tools -> Compilation). Any ideas?
And just checked after reading other comments regards using correct version of patches – the version is same (1.8.1.0 ) in both test shop and main site. Thanks
Hello @Colin,
I see you have tried in test environment and live both but live website still showing vulnerable, Was compilation enabled on your live store? You should disable it before making any changes in the website. Please run the compilation again and check flush all the external cache if you are using in the Magento including default cache. Then check the website, if you still face the issue, do contact us, we will be happy to help you out.
Thanks it works disabling compilation and apply patches and reactive compilation
Hello @Christophe
Nice to hear 🙂 Cheers
Thanks – in the end I broke each zip file down into its individual file and dropped each file it into the relevent folder — worked finally! Thanks for your help very much appreciated:)
Uploaded the file to the magento directory, and ran the SH script — I’m receiving the following:
Checking if patch can be applied/reverted successfully… ERROR: Patch can’t be applied/reverted successfully.
can’t find file to patch at input line 5 Perhaps you used the wrong -p or –strip option?
The text leading up to this was:
|diff –git app/code/core/Mage/Admin/Model/Observer.php app/code/core/Mage/Admin/Model/Observer.php |index bd00181..6a5281c 100644 |— app/code/core/Mage/Admin/Model/Observer.php
|+++ app/code/core/Mage/Admin/Model/Observer.php
File to patch: Skip this patch? [y] Skipping patch. 3 out of 3 hunks ignored can’t find file to patch at input line 46 Perhaps you used the wrong -p or –strip option?
The text leading up to this was:
|diff –git app/code/core/Mage/Core/Controller/Request/Http.php app/code/core/Mage/Core/Controller/Request/Http.php |index 6513db9..31eb6d6 100644 |— app/code/core/Mage/Core/Controller/Request/Http.php
|+++ app/code/core/Mage/Core/Controller/Request/Http.php
File to patch: Skip this patch? [y] Skipping patch. 2 out of 2 hunks ignored can’t find file to patch at input line 91 Perhaps you used the wrong -p or –strip option?
The text leading up to this was:
|diff –git app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php |index c30d273..36542f9 100644 |— app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php
|+++ app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php
File to patch: Skip this patch? [y] Skipping patch. 1 out of 1 hunk ignored can’t find file to patch at input line 104 Perhaps you used the wrong -p or –strip option?
The text leading up to this was:
|diff –git app/code/core/Mage/XmlConnect/Model/Observer.php app/code/core/Mage/XmlConnect/Model/Observer.php |index e6cb947..36142ac 100644 |— app/code/core/Mage/XmlConnect/Model/Observer.php
|+++ app/code/core/Mage/XmlConnect/Model/Observer.php
File to patch: Skip this patch? [y] Skipping patch. 2 out of 2 hunks ignored can’t find file to patch at input line 126 Perhaps you used the wrong -p or –strip option?
The text leading up to this was:
|diff –git lib/Varien/Db/Adapter/Pdo/Mysql.php lib/Varien/Db/Adapter/Pdo/Mysql.php |index 2226331..d1c6942 100644 |— lib/Varien/Db/Adapter/Pdo/Mysql.php
|+++ lib/Varien/Db/Adapter/Pdo/Mysql.php
File to patch: Skip this patch? [y] Skipping patch. 1 out of 1 hunk ignored
Hello @Aj,
Are you using Magento 1.9, I would suggest you to go with the 3rd Method if you are getting this one.
Hi,
Please assist.
I uploaded the file /Varien/Db/Adapter/Pdo/Mysql.php because I get the following error when doing it via SSH
1 out of 1 hunk FAILED — saving rejects to file lib/Varien/Db/Adapter/Pdo/Mysql.php.rej
But after I replace the file I get the error below.
Fatal error: Class Varien_Db_Adapter_Pdo_Mysql contains 8 abstract methods and must therefore be declared abstract or implement the remaining methods (Varien_Db_Adapter_Interface::createTemporaryTable, Varien_Db_Adapter_Interface::dropTemporaryTable, Varien_Db_Adapter_Interface::renameTablesBatch, …) in
I would really appreciate some guidance
Hello @Dale,
It seems you haven’t installed the patches of compatible Magento version. Will you please verify once?
After applying the patches last weekend and my sites tested as “SAFE”, I still got hacked earlier today!
A new administrator account was made and I was locked out of the admin panel. Even after changing my user/password via PHPMyAdmin, I couldn’t log in. Every time I got a “access denied” error.
I had to completely restore an older Db backup to get access again and I’ll have to check ALL the Magento files and folders again to see if there where any changes made to them.
Consider this a warning to everybody who think they are safe after applying these two patches….YOU ARE NOT!
Check every file against an older backup!
# bash ./PATCH_SUPEE-1533_EE_1.13.x_v1-…
Checking if patch can be applied/reverted successfully…
Patch was applied/reverted successfully.
# bash ./PATCH_SUPEE-5344_CE_1.8.0.0_v1…
Checking if patch can be applied/reverted successfully…
Patch was applied/reverted successfully.
I got these. But if I test it here ( https://magento.com/security/patches…, I am getting warning “WARNING: This site appears to be vulnerable. Please patch it immediately!”
What should I do now ??
Hello @Foysal
PLease contact us on support@magecomp.com along with the Magento admin and cpanel details, we will be happy to help you out.
its giving error: ERROR: “/app/etc/” must exist for proper tool work.
Hello @sohrab,
Which patch and which method you are trying to install the patch, please do contact us if you need help with the patch installation.
What about 5994 for Magento 1.3?
I have one client I inherited with a heavily modified 1.3 core and no budget that I need to find a 5994 solution for.
Thanks!
Hello @Joshua,
We have just updated the patches for Magento 1.4, we are constantly trying to help all the customers using any Magento version. We will update the blog soon with the patch solution for Magento 1.3 as well.
However, I would also suggest to go with latest version of Magento, either by upgrading or by Migrating, as there are lot more features and security patches implemented.
That is excellent news. Yes I agree and have updated all clients I can to the latest version. This one client has a heavily modified magento though and no budget to port those modifications to a newer version at this time. So in this one case the 1.3 patch will be a lifesaver!!! Thank you so much! Cheers.
Would you be able to provide a zip of the patched files for Magento CE 1.8.0.0 with the May 14th patch 5994?
I keep getting the below error when trying to apply the 5994 patch for my version, on my dev environment:
patch: **** misordered hunks! output would be garbled
Patch file used, downloaded from Magento: PATCH_SUPEE-5994_CE_1.6.0.0_v1-2015-05-15-04-34-46.sh
Patch command used: sh
Any help to resolve this would be much appreciated!
Hello @Catherine,
You can use the zip package of Magento 1.8.1.0,just make sure to take backup of the files you are overwriting. It is also recommended to upgrade your Magento version to the latest one asap.
Have you got a patch – SUPEE 5994 Patch for 1.7.0.1?
Hello Amanda,
You can use the patch of 1.7.0.2 and install it, make sure to take backup of the files you are overwriting.
Hi,
I have installed two patches 5344, 1533 but it is still staying it is valuable, can you please help?
I installed these two patches on the other site yesterday and they worked fine.
Thank you
Yes you can contact us on support@magecomp.com with the required details.
My magento store is version 1.9.0.1 and installing the patch 5994 causes me the error that customers can not buy as guests. I would greatly appreciate that indicate me how to solve this problem.
Can you please drop us an email with the details at support@magecomp.com?
Hi, Tried to apply this fix on version 1.9.0.1 but get the following error, anyone got any ideas? surely thisfix doesn’t have a bug!!
Parse error: syntax error, unexpected T_CLASS in /home/www/../PATCH_SUPEE-5994_CE_1.6.0.0_v1-2015-05-15-04-34-46.sh on line 338
Why I think so that you are installing wrong patch for your Magento version. Please make sure you are installing the patch of Magento 1.9
Hi there!
I’m trying to run method 1 for PATCH_SUPEE-6285 and I’m getting the error:
“/app/etc/” must exist for proper tool work.
NOTE: this is on a dev. domain, where there is a live install in the root, and the dev site is installed under /dev
Any ideas?
Thanks!
Please make sure you have uploaded the patches in the root of the Magento and in ssh you are at the same path (root of magento installation) while running the patch.
If problem still persist, do contact us on support@magecomp.com, we will be glad to help you out.
Thanks for the post! Will you release files for SUPEE 6285 on magento 1.5?
We are working on it, we will launch it soon,
I have applied version 1 of 6285 but as advised by magento need to apply the version 2. I have tried reverting the version 1 by using the command in putty but get the following error “sh: PATCH_SUPEE-6285_CE_1.9.1.1_v1-2015-07-10-08-10-09.sh: No such file or directory”
I have checked the patch history and it has been applied and I can see that in applied.patches.list
Can you please advise?
Hello @Farhad,
Make sure you are at the path of root installation of Magento and make sure the patch file name. What command you are using to revert the v1 patch?
Enter the following command as a user with sufficient privileges to write to Magento files (typically, the web server user or root):
sh patch-file-name.sh -R
I have just done the security patch updates on a magento 1.6.0 site. They all seemed to install ok by SSH. Before installation I turned off compiler and created a Router directory. then once installed site seemed ok, went into admin to clear the cache’s I did flush mangento cache and also checked all the cache’s in the list and did a refresh, at this point my admin and site went blank, nothing in the pages at all. Help!
We have applied the patch as per your suggested method #3 for Magento 1.9.0.1. When we tried to reverse the patch, we are receiving an error which states – “Unreversed Patch detected!”
Please assist us how to to reverese the previously applied patch and reapply the new one which Mageto released couple of days back.
With Thanks!
Sam
Hello @Sam,
If you have installed v1 patch using our zip file method, then no need to revert. Just install new version patch files and don’t forget to take backup 🙂
Howdy,
I used the Patch.php method to apply the latsest security patch, now I have a message that I have to revert the patch and install newest version of the patch.
is there a way to revert the patch using the patch.php method?
I noticed using SSH that it was possible adding a “-r” at the tail end of the patch name and run it, can I do the same thing?
Thanks!
Ken
Howdy,
This line added because it says I already posted this comment …
I used the Patch.php method to apply the latsest security patch, now I have a message that I have to revert the patch and install newest version of the patch.
is there a way to revert the patch using the patch.php method?
I noticed using SSH that it was possible adding a “-r” at the tail end of the patch name and run it, can I do the same thing?
Thanks!
Ken
Thanks for your prompt response!
Are you suggesting that i need to use method #3 again with the updated files?
Secondly, How one can uninstall the patch if used method #3 as described in your blog page?
Please advise.
With Thanks!
Sam
Hello @Sam,
You don’t need to uninstall the patch if you have used our Method 3. So you can overwrite the new patched files directly. Just take care of the backup of the files.
Hello @Ken,
Yes you will need to revert the patch as you have installed the patch using Php file method, you can add -R at the end of the patch name same like need to do with SSH command,
Let us know,
Thanks, I am new in Magento developing and your article very useful for me thanks again.
hi there,
i m using magento ver. 1.9.1.0 i tried applying SUPEE-6285 patch method 1 it just says done. i kept patch file and patch.php in the root folder. how do i know if its patched or not can you plz help me.
tks in advance
John
Hello @John,
If you have installed the patch using SSH or Php file method, you will be able to check the installation using our Magento Applied Patches extension.
You can try even reading applied.patches.list at app/etc
hi i checked inside app/etc but i cant find the file i used patch.php to patch. i downloaded the file you provided me in the link it show this error (Fatal error: Class ‘Magecomp_AppliedPatches_Helper_Data’ not found in). what can be the problem.
thanks
john
Hello @john,
Are you sure you have installed the patches properly? Because if you use patch.php, applied.patches.list file should be created which can be read by our extension. Also make sure you have installed Applied patches extension properly.
Thanks
I installed the patch 5344 and 5994 on my magento 1.9.0.1 . For 1 week all worked properly but now I get a 500 error when trying to access the web . Is there a causal relationship between installing patches and the appearance of this error.
Hello @Atntonio
There shouldn’t be related to patches, did you try to take backup of your Magento store. or do you remember last changes or last extension install?
That may cause the issue,
If you don’d find any of them, you can surely contact us at https://magecomp.com/contact
We will be gald to help you out.
Hello,
i have a live side in magento 1.8.1.0 and i don’t install any magento security patches,
can you please help me how many patches i need to install
thanks.
Hello @Hardik,
You are requested to place order for the security patches installation here, we will be happy to help you out.
https://www.magecomp.com/magento-security-patches-installation.html
Thank you so much for this! I have been having issues installing through my cPanel, not sure why, so having Method 3 available was amazing!
Glad to hear @Amanda, it helped 🙂
Do these work for 1.9.2.0?
Hello @Rose,
Magento 1.9.2 already has all the patches, except SUPEE 6285 v2. So I would suggest to change the file which has been changed in v2.
Please read this thread for more information
http://community.magento.com/t5/Technical-Issues/magento-patch-6285-v2/m-p/10609
I would also install security extension like this one: http://magentools.com/work/magesecure-magento-security-extension/ to protect Magento store.
Thanks for the article!
thank you for the 6482 files. Helps me out a lot. Cheers!
Can you teach me how did you apply this patch-6482? I downloaded the zip files from magento, so do I unzip them and drag all the folders into FTP folder and it will auto-update the files and replace where necessary?
I dont have access to SSH so cant do it the SSH way.
Hello @Michelle,
Yes please unzip the files, go to the relevant path in your Magento, backup your original file, and upload the package file using FTP.
Do same for other files.
i have done all the code in patch.php with file name and put .sh file in bin folder. but when i put the ptach.php path on url its show the msg “done”. after that when i login into magento admin thn its show again the msg patch error.
Hello @mohit
Don’t worry about the message, that message is just the notification from Magento. There is no relation with the patch installed or not. if you have installed the patch correctly, you can just mark that message as read so it won’t show again.
Great help with getting this patch sorted, as I had the “Hunk” failed error … many thanks!!!
Hello @Joe,
You are most welcome 🙂 Be in touch for Magento news, guides and turorials.
Thanks for these how-to’s! If you want to be sure you’ve installed them write, please check via https://www.magereport.com. It’s a security check website developed by Magento hostingprovider Byte. We found out that strangely enough 80% of all Magento installations worldwide haven’t installed all patches ..
Hi,
It’s possible more than one patch file will install in Magento ..?
You will need to install the patches according to the Magento version you are using?
You will find the list of patches you will need to install on your Magento (depending on Magento version you are using)
https://docs.google.com/spreadsheets/d/1MTbU9Bq130zrrsJwLIB9d8qnGfYZnkm4jBlfNaBF19M/edit#gid=192164130
Hello, I am using magento 1.4.1.1 version and when I log in on admin panel magento show me message to install immediately patches 6788 but there is no version of 6788 for magento 1.4.1.1. How could I install PATCH 6788?
i’m using Magento Security Patch (SUPEE-6788) this patch in my site and my website magento version 1.8.1.0 when i’m reun patch show me message done but i’m show still msg in my admin panel please guide me
Hello asma,
The message you can see is, just a notification. You can mark it as read and it won’t display again.
Hi,
get the following message when trying to install the patch:
PATCH_SUPEE-6788_CE_1.9.1.0_v1-2015-10-27-09-06-11.sh: 14: PATCH_SUPEE-6788_CE_1.9.1.0_v1-2015-10-27-09-06-11.sh: 127: not found
PATCH_SUPEE-6788_CE_1.9.1.0_v1-2015-10-27-09-06-11.sh: 14: PATCH_SUPEE-6788_CE_1.9.1.0_v1-2015-10-27-09-06-11.sh: 127: not found
PATCH_SUPEE-6788_CE_1.9.1.0_v1-2015-10-27-09-06-11.sh: 25: PATCH_SUPEE-6788_CE_1.9.1.0_v1-2015-10-27-09-06-11.sh: 0: not found
Checking if patch can be applied/reverted successfully…
-e ERROR: Patch can’t be applied/reverted successfully.
patching file .htaccess
Hunk #1 FAILED at 207.
Any help would be appreciated! Thank you in advance!
We have updated the blog, please have a look at few commands we have added. Those will help you for easy installation of patches.
If you still need help, feel free to contact us anytime.
Hi there
each time i run in browser it has this msg
Warning: passthru() has been disabled for security reasons in /home/jewelman/public_html/patch.php on line 3
Done
please advise as we do have hackers adding themselves to admin:-(
Remove the passthru string from the disable_functions at php.ini* file if you have access, or you can ask hosting provider.
Hi there. I am having the exact same problem as Ash
Warning: passthru() has been disabled for security reasons in /home/jeweller/public_html/new/patch.php on line 3
I cannot locate the file php.ini. I can only find php.ini sample. Can you give me the patch of where I can find this file and exactly what the string will say so I know what I am lookng for.
Your help would be greatly appreciated.
Thank you
Hello ann,
If you are on shared hosting, you won’t be able to access the php.ini file, please ask your hosting provider to make necessary change.
Hi there , Thank you for your help I have asked my hosting company to do this for the patch 5994 as it seems this one needs to be done ssh, if I am not mistaken. they have removed the pass thru but the patch is stil not installed. When you run the patch command in the brower all you get is Done. Now when you go to my webside I get the following error on my product and the add to cart button no longer works. I have reverted back to them but wonder if you could help with this.
Fatal error: Call to a member function getFrontend() on a non-object in /home/jeweller/public_html/new/app/code/local/Infortis/Brands/Block/Abstract.php on line 5
Also for the 6285 patch, you say to upload all files. Sorry I know it is probably easy and you say to do use the same process as patch 1533. Do you mean the same path? Can you give me the actual path to use please or the individual paths I need to take .
Any help is gratefully appreciated.
Hello Ann,
I would suggest to contact our technical team at support@magecomp.com with the help of installing security patches.
I’VE BEEN HACKED this morning!
Even after applying all patches the last months. I can not login to my admin anymore and the added two folders to my JS-folder (editor + filesystem) I tried to alter my password with PHPmyadmin, but still I can’t get access.
Magento 1.9.2.2
Hello Berry
Please contact us at support@magecomp.com and our Magento technical team will help you to secure your Magento store and help you with your issue as well,
I am having some trouble installed patch 5344.. I hope you can help.
Checking if patch can be applied/reverted successfully…
ERROR: Patch can’t be applied/reverted successfully.
patching file app/code/core/Mage/Admin/Model/Observer.php
Reversed (or previously applied) patch detected! Assume -R? [n]
Apply anyway? [n]
Skipping patch.
3 out of 3 hunks ignored — saving rejects to file app/code/core/Mage/Admin/Model/Observer.php.rej
patching file app/code/core/Mage/Core/Controller/Request/Http.php
Reversed (or previously applied) patch detected! Assume -R? [n]
Apply anyway? [n]
Skipping patch.
2 out of 2 hunks ignored — saving rejects to file app/code/core/Mage/Core/Controller/Request/Http.php.rej
patching file app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php
Reversed (or previously applied) patch detected! Assume -R? [n]
Apply anyway? [n]
Skipping patch.
1 out of 1 hunk ignored — saving rejects to file app/code/core/Mage/Oauth/controllers/Adminhtml/Oauth/AuthorizeController.php.rej
patching file app/code/core/Mage/XmlConnect/Model/Observer.php
Reversed (or previously applied) patch detected! Assume -R? [n]
Apply anyway? [n]
Skipping patch.
2 out of 2 hunks ignored — saving rejects to file app/code/core/Mage/XmlConnect/Model/Observer.php.rej
patching file lib/Varien/Db/Adapter/Pdo/Mysql.php
Reversed (or previously applied) patch detected! Assume -R? [n]
Apply anyway? [n]
Skipping patch.
1 out of 1 hunk ignored — saving rejects to file lib/Varien/Db/Adapter/Pdo/Mysql.php.rej
Hope you got the solution now, after contacting us. 🙂
Hello i tried to install SUPEE 5994 i’m using magento 1.4.2.0 a message apprers “done” but nothing change how can i do to resolve yhis probem thank you in advance
Did you check your website in magereport.com?
Hi I am facing the error number 8.I try the solution also at the specific line number code is present there.But don’t know still facing the similar issue.
patching file app/code/core/Mage/Adminhtml/Helper/Sales.php
Hunk #1 FAILED at 121.
Any help will be appreciated.
Thanks
Did you try to get the same file from the default and same version of Magento?
Do you have “security patch” for magento 1.9.2 version ?
Which security patch you want for 1.9.2?
Please have a doubt:
Have any trouble installing SUPEE_8788_Magento_1.9.2.4 in Magento 1.8.1?
In is not possible now to upgrade to 1.9.2.4.
This prepatched file may not work for Magento 1.8.1, the better option to get Magento version upgraded to 1.9.3
Hello MageComp,
I just want to see about compatibility for the new security patch SUPEE 8788. I noticed you guys say the zip file for it is for Magento version 1.9.2.4. Will this also work for 1.9.2.2? This would be the version we are running :). As all ways thanks for the awesome work you guys do here!
Shawn
If you have installed all previous patches, it should work.
Thanks guys! Just installed and it works great! I did how every notice the first time uploading an image to a product the browse and upload button shifted to the left. They are supposed to be on the right of course. I refreshed my browser and poof… they went back to normal and working normal lol. So heads up to anyone that this might happen to.. just refresh your web browser.
Thanks for sharing your experience.
Hello can you upload patch for 1.9.2.3 and 1.9.2.0 please so i can install without ssh please i need full package. thanks in advance
I installed patch 8788 by hand and https://shoplift.byte.nl/ shows my site is patched, but on my admin page it still shows as Magento ver. 1.9.2.3 ?
Installing patches doesn’t upgrade Magento version, you will need to updgrade your Magento version to see 1.9.3 at the bottom of admin.
this blog is very useful
Hi
Can you make SUPEE-8788-V2 available for magneto 1.8.1. i can’t seem to see it in the file options on github?
it seems to jump from 1.7 to 1.9?
I know I’m way behind!! But looking to upgrade to 2 shortly.
Thanks
Hi,
I want SUPEE 5344 for magento CE version 1.9.2.1 to install SUPEE 8788
Hi,
I need your help I have successfully installed SUPEE-8788 version v2 but it’s showing 404 error: Page not found. for both frontend and backend for magento version 1.9.2.1
Please contact us from our contact form.
Can you please also write code for revert patches through php script ? as you wrote for apply patches trhough php script ?
Code is already shown in Method 1
< ?php print(""); passthru("/bin/bash PATCH_SUPEE-8788.sh"); print("");
echo "Done";
?>
Upload script, upload patch file and run
just shows Done when execute patch.php from the browserbut not showing in applied patches
Can you try checking in magereport?
“sh patch-file-name.sh” Replace this with “sh patch-file-name.sh -R” in script.
Hi admin where is the exact location to upload the patches via ftp ?
You will need to upload the Patch files in the root of your Magento.
As all ways thanks for everything you guys do. SUPEE-9652 installed and everything is still working smoothly. Cheers guys!
Glad to hear 🙂
Hi,
Can i get Security patch 9767 for magento 1.9.1.1
plz
We install PATCH_SUPEE-7405_CE_1.9.2.0_v1.1-2016-02-23-07-41-47.sh
in Method – 1 but not to applied show this massage
Checking if patch can be applied/reverted successfully…
ERROR: Patch can’t be applied/reverted successfully.
patching file app/code/core/Mage/Adminhtml/Helper/Sales.php
Hunk #1 FAILED at 121.
1 out of 1 hunk FAILED — saving rejects to file app/code/core/Mage/Adminhtml/Helper/Sales.php.rej
patching file app/code/core/Mage/Core/Model/Config.php
Hunk #1 FAILED at 1642.
1 out of 1 hunk FAILED — saving rejects to file app/code/core/Mage/Core/Model/Config.php.rej
patching file app/code/core/Mage/Sales/Model/Quote/Item.php
Hunk #1 FAILED at 507.
1 out of 1 hunk FAILED — saving rejects to file app/code/core/Mage/Sales/Model/Quote/Item.php.rej
patching file lib/Varien/File/Uploader.php
Hunk #1 FAILED at 216.
Hunk #2 FAILED at 538.
2 out of 2 hunks FAILED — saving rejects to file lib/Varien/File/Uploader.php.rej
Done
Please help me urgent
Please check our FAQ section for Hunk Failed issue
Please check the FAQ no. 8
Have any trouble installing SUPEE_8788_Magento_1.9.2.4 in Magento 1.8.1?
In is not possible now to upgrade to 1.9.2.4.